We understand the critical importance of rock-solid cybersecurity. We offer a comprehensive range of services tailored to meet the unique needs of businesses of all sizes, from small and medium-sized enterprises (SMEs) to large corporations.
Threat Detection & Response
Data Breach Prevention
Compliance & Risk Management
Cybersecurity Solutions for Small Businesses
Managed Detection and Response (MDR)
Provides continuous monitoring of your network, detecting and responding to threats in real-time. Access to a team of cybersecurity experts who manage and mitigate threats, reducing the burden on your internal IT staff. Offers comprehensive protection without the need for extensive in-house resources, making it an affordable solution for SMEs.
Multi-Factor Authentication (MFA)
Adds an extra layer of security by requiring multiple forms of verification to access systems, significantly reducing the risk of unauthorized access. Easy to implement and use, ensuring minimal disruption to daily operations while enhancing security. Helps meet regulatory requirements and industry standards, protecting your business from potential fines and legal issues.
Employee Training and Awareness Programs
Educates employees on recognizing and responding to phishing attempts, reducing the risk of data breaches caused by human error. Regular training sessions keep employees updated on the latest cybersecurity threats and best practices, fostering a culture of security awareness. Prevents costly cyber incidents by empowering employees to act as the first line of defense against cyber threats.
Cybersecurity Audit Services
Our cybersecurity services near me in-depth cybersecurity audits proactively identify and mitigate cyber threats. Gain valuable insights to strengthen your defenses and safeguard your business.
- Risk Identification
- Compliance Assurance
- Performance Optimization
- Threat Detection
- Secure Development
- User Trust
- Data Protection
- Access Control
- Regulatory Compliance
- Device Security
- Policy Enforcement
- Incident Response
- Network Protection
- Signal Integrity
- Compliance Verification
- Data Integrity
- Encryption Practices
- Policy Compliance
- Proactive Defense
- Realistic Testing
- Continuous Improvement
- Regulatory Adherence
- Risk Mitigation
- Audit Readiness
- Human Factor Security
- Phishing Resistance
- Behavioral Insights
Cybersecurity Compliance Services
Ensure your organization meets advanced industry standards and protects sensitive data.
 GDPR Compliance
GDPR Compliance
Ensure compliance with the General Data Protection Regulation (GDPR), the EU's stringent data privacy law. Protect your organization from hefty fines and legal repercussions. Build trust with customers and demonstrate your commitment to data privacy.
 HIPAA Compliance
HIPAA Compliance
Adhere to the Health Insurance Portability and Accountability Act (HIPAA) regulations for protecting patient health information (PHI). Maintain patient trust and avoid costly fines and penalties. Improve the security of your healthcare operations and patient data.
 PCI DSS Compliance
PCI DSS Compliance
Comply with the Payment Card Industry Data Security Standard (PCI DSS) for handling credit card data. Prevent data breaches and protect your organization from fraud and financial loss. Maintain a secure payment processing environment and build customer trust.
 NIST Cybersecurity Framework Compliance
NIST Cybersecurity Framework Compliance
Implement the National Institute of Standards and Technology (NIST) Cybersecurity Framework to improve your overall cybersecurity posture. Identify, assess, and manage cybersecurity risks effectively. Enhance your organization's resilience against cyber threats.
Our client say
Michel Bielecki
CEO & Co-founder of Testasy
“O16 Labs ultimately delivered a working product, allowing me to launch a unique service worldwide. The team was quite responsive, transparent and supportive throughout. They all worked really hard and fast, demonstrating amazing ability to deliver market-ready MVP swiftly”
George Bardakis
Digital Communications Director, Bet Comrade
“O16 Labs worked tirelessly and consistently throughout the project collaboration, always ensuring high-quality outcomes. The team is always responsive, available and effortlessly accommodates to concerns and queries, thus providing top-tier assistance. Their skills, responsiveness and impeccable communications surpassed clients’ expectations.”
 Spain
Spain
Nicolas Adolph
Founder of DocuDoc
“The outcome of partnering with O16 Labs has been highly favorable. The team is agile and utterly collaborative from a project management point of view. Internal stakeholders were impressed by the service provider’s patience and professionalism.”
 Pakistan
Pakistan
Waseem Sindhu
Director of Technology from a Digital Marketing Agency
“Thanks to the work from O16 Labs, the client reached a whopping 200,000 downloads just within two months and secured 10,000 active monthly users. They communicated actively and effectively via Slack and Trello. Their transparency and project management styles have been hallmarks of their work.”
Woodrow Jones
Co-founder and CEO of Vibecoin
O16 Labs have all it takes to meet clients’ expectations in terms of process and delivery timelines. The team remained highly responsive and offered expert consultancy on app development. Their ability to listen and adapt to clients’ suggestions is highly plausible, allowing them to further extend their expertise in blockchain development.”
Stephanie Phillips Fokas
Director of Patient Advocacy, Overwatch Digital Health
“Ever since O16 Labs took over the project, deliverables have been outstanding. The team is well-versed, fully-prepared and actively participates in meetings. Their sense of urgency and grasp on a project is fantastic.”
Our Cybersecurity Defense Services
Cybersecurity experts near me cover major cybersecurity defenses that can protect your business from evolving threats.
Network Security Defenses
Network firewalls act as a barrier between your internal network and the external internet, blocking suspicious traffic and unauthorized access. IDPS monitor network traffic for signs of unauthorized access or malicious activity, alerting security teams to potential threats. VPNs encrypt internet traffic to protect sensitive data transmitted over public networks.
Endpoint Security Defenses
Antivirus software detects and removes malware, including viruses, Trojans, and spyware. EDR solutions monitor endpoint devices for signs of malicious activity, providing real-time threat detection and response. Device management solutions enable IT teams to remotely manage and secure endpoint devices, ensuring compliance with security policies.
Application Security Defenses
Secure coding practices ensure that software applications are developed with security in mind, reducing the risk of vulnerabilities. WAFs protect web applications from common web exploits, such as SQL injection and cross-site scripting (XSS). Vulnerability management solutions identify and remediate vulnerabilities in software applications, reducing the risk of exploitation.
Data Security Defenses
Encryption solutions protect sensitive data by converting it into an unreadable format, ensuring that only authorized parties can access it. Access control solutions ensure that only authorized personnel have access to sensitive data, reducing the risk of insider threats. DLP solutions monitor and control sensitive data in motion, preventing unauthorized data exfiltration.
Develop a Winning B2B Cybersecurity Strategy
A robust cybersecurity strategy is essential for the success of any modern business. We follow these five key steps to protect your organization from evolving threats
01 Conduct Risk Assessment
Identify and prioritize the most critical cyber threats facing your organization. Analyze the potential impact of these threats on your business operations, reputation, and finances. Gain a clear understanding of your current security posture and identify areas for improvement.
02 Define Security Objectives
Establish clear and measurable security goals that align with your overall business objectives. Ensure that your security initiatives support your business growth and innovation. Create a framework for evaluating the effectiveness of your cybersecurity program.
03 Implement Security Controls
Implement a layered approach to security, incorporating a combination of technical, administrative, physical, and human controls. Choose the right security technologies and solutions to protect your critical assets. Ensure that your security controls are effectively implemented and maintained.
04 Culture of Security
Educate your employees about cybersecurity threats and best practices through training and awareness programs. Encourage employee participation in security initiatives and promote a culture of security within your organization. Reduce the risk of human error and social engineering attacks.
05 Monitor and Improve
Regularly review and update your cybersecurity strategy to adapt to the evolving threat landscape. Conduct regular security audits and assessments to identify and address any vulnerabilities. Continuously improve your security posture through ongoing monitoring, evaluation, and refinement.
Successful Cybersecurity Engagements
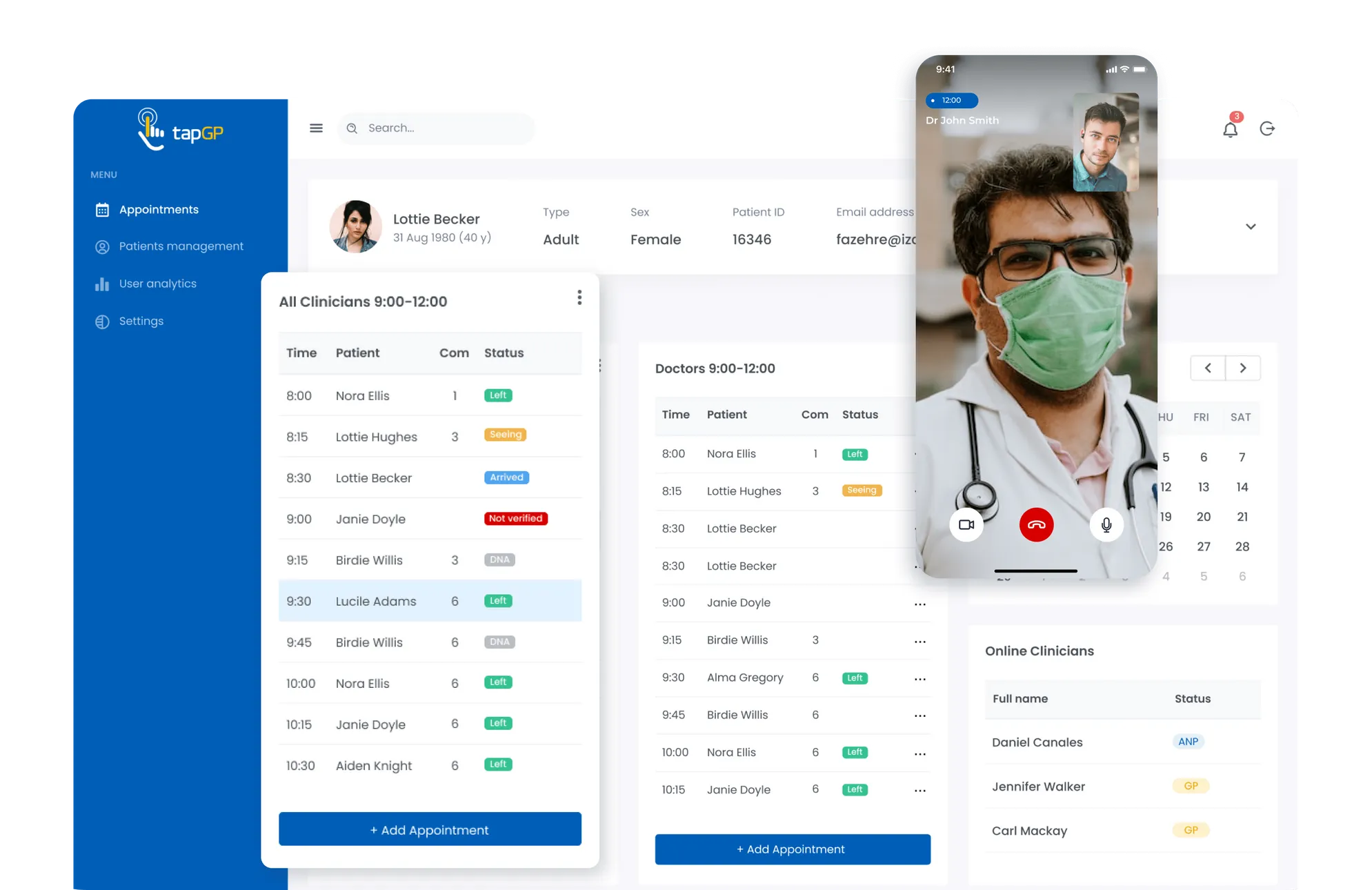
A Telemedicine System For Appointments Management
Creation of a Telemedicine System For Appointments Management
Challenges solved:
- Development of the SaaS for providing and receiving telecare services
- Providing 24/7 online access to video and audio consultations of general practitioners and clinicians
- Creation of an online appointment booking functionality
- Compliance with the requirements of GDPR and UK healthcare regulators (CQC and MHRA)
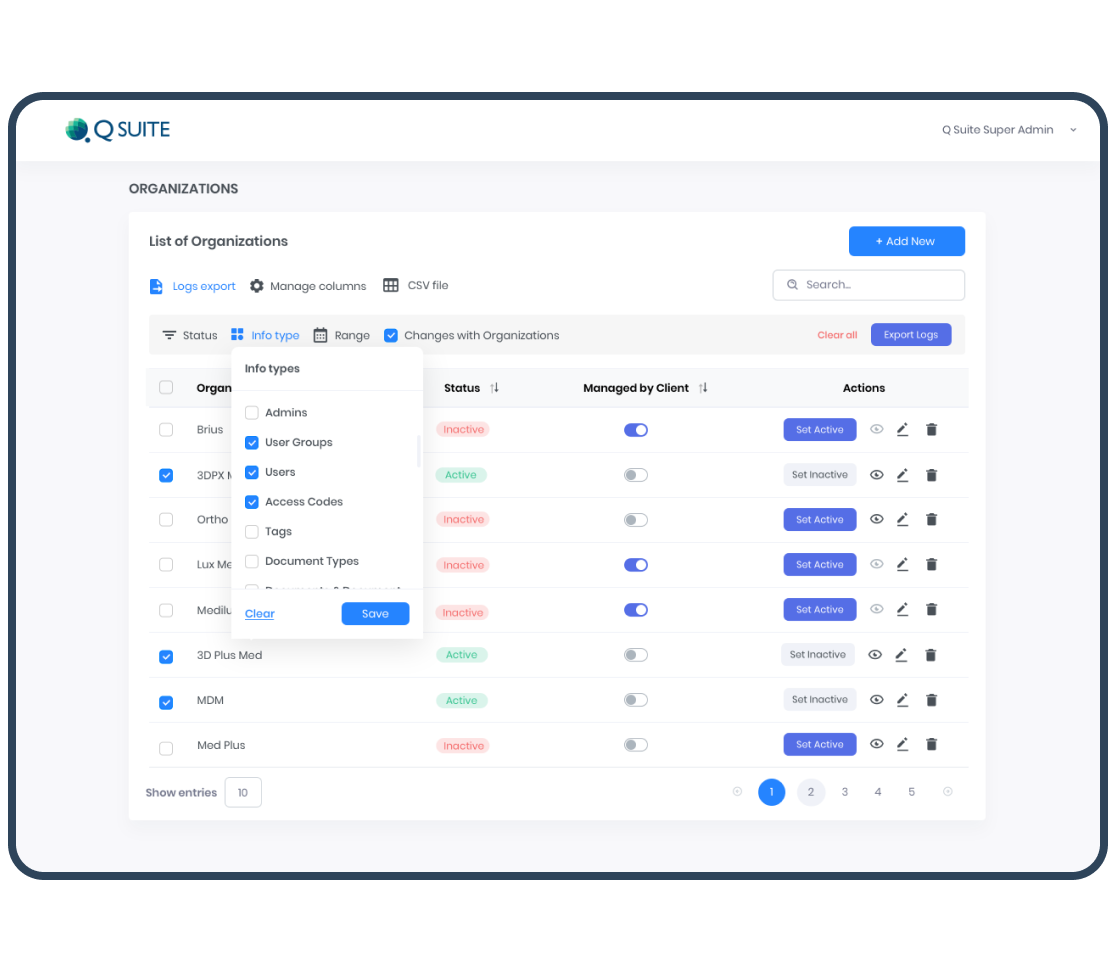
QMS for Medical Device Manufacturers
Development of a Quality Management System to Check FDA/ISO Compliance
Challenges solved:
- Development of a Quality Management System (eQMS) from scratch
- Automation and UX improvement of document flow and processes of FDA/ISO certification
- Creation of a B2B SaaS to check compliance to FDA 21 CFR 820, 21 CFR 11 and conformance to ISO 13485:2016 and MDSAP
Best-in-Class Cybersecurity Technologies
We utilize a robust and constantly evolving technology stack to provide cutting-edge security solutions for our clients.















